Red Teaming
VAPT and Config Audits
Wireless Security / Cloud Security
Network Security Architecture Review
Red Teaming Service
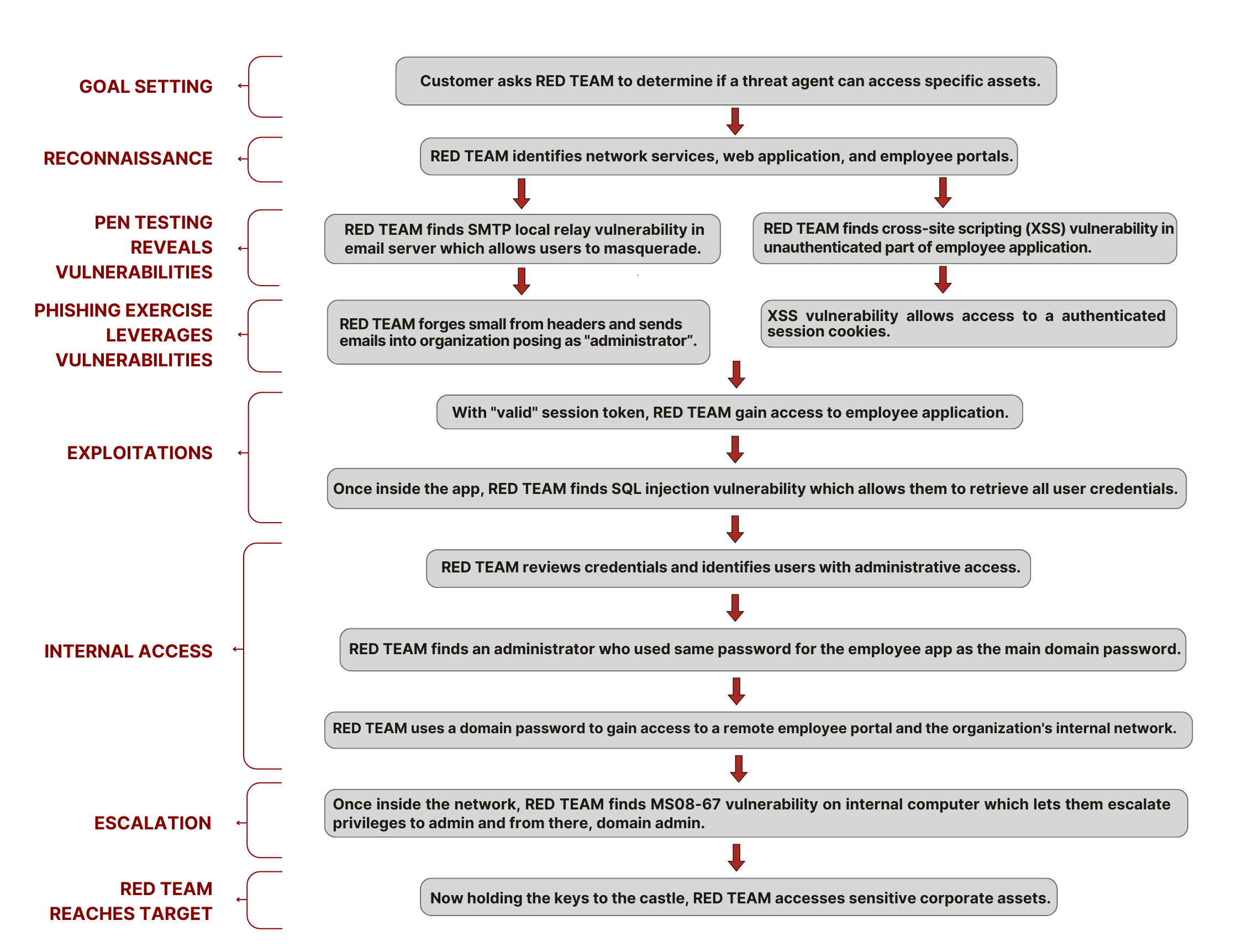
Why choose Anzen for your Red Teaming Assessment ?
Anzen Technologies provides the following benefits to organizations for their Red Teaming assessment requirement
- Team of experienced offensive security experts
- Collectively more than 10 years of experience in providing Red Teaming services
- Multi-layered Assessment approach
- State-of-the-art Exploitation lab setup for remote assessments
- Updated with latest technological advancements (Cloud, Virtualization, mobile etc.)
- Additional support for closure of findings (if required)
- Tailor-made separate Executive & Technical Reports and Dashboard

Vulnerability Assessment & Penetration Testing (VAPT)
- Read More
- Vulnerability Assessment is used to identify known vulnerabilities in a network or operating system/server at an application level.
- Through this assessment we provide an organization with an overall picture of all the vulnerabilities present on their network infrastructure.
- We also extend our services by assisting in vulnerability mitigation and risk management.
- In Penetration testing, our experts analyse your network infrastructure or specific assets from the point of view of a malicious hacker who is trying to gain unauthorized access or trying to execute actions through elevated privileges.
Secure Configuration Audit
- Read More
- The purpose of a Configuration Audit is to protect the organization’s assets from sophisticated, targeted long-term attacks where hackers gain access to privileged systems and data. Even a zero-day attack has less of a chance of resulting in a security breach in a securely configured system.
- Secure configuration refers to security measures that are implemented when building and installing computers and network devices to reduce unnecessary cyber vulnerabilities. Security misconfigurations are one of the most common gaps that criminal hackers look to exploit.
BENEFITS OF SECURE CONFIGURATION AUDIT
- Protect data integrity and avaliability
- Make it scalable for future needs
- Improve performance
Wireless Security Assessment
Wireless Networks are an integral part of organizations' network infrastructure and have exposure to internal/external threats.
Assessment details
- Read More
- Wireless networks are essential for any organization’s network infrastructure but are also highly vulnerable to threats.
- Anzen’s wireless security audit methodology is based on extensive research, proven techniques, advanced tools, and the experience of our security experts.
- Goal: To maximize coverage against the various dimensions of threats that wireless networks may face.
- Wireless deployments extend beyond the physical premises, which introduces unique security risks in which attackers can target access points using pre-defined strategies.
- These assessments help in identifying, locating, and mitigating risks associated with the current implementation of wireless network technology.
- The assessments are conducted using a pragmatic & systematic approach to evaluate and report the current security posture of the network.
Anzen Approach
- Read More
- Defining Testing Scope.
- Detection of Wireless Access Points as well as Rogue Access Points.
- War Driving.
- Wireless Network Vulnerability Scanning.
- Vulnerability Identification & Validation.
- Wireless Device Configuration Review & Report.
Cloud Security Assessment
The goal of a cloud security architecture review is to identify and highlight cloud security weaknesses and strengths and provide guidance towards building a mature cloud security architecture. Anzen’s cloud security architecture review process helps in mapping out the attack surface, identifying attack vectors and evaluating the threats.
Assessment details
- Read More
- First, a Data Flow Diagram (DFD) of the cloud infrastructure is reviewed.
- A Threat Model of the cloud infrastructure will be created.
- Non-Functional Security Requirements (NFSR) documents that highlight security best practices and hardening guidelines of the entire technology stack in scope will be created.
- Finally, Gap Analysis will be done.
Network Security Architecture Review
Assessment details
- Read More
- ANZEN network architecture review is a process of thoroughly assessing the network component’s configurations with their
placements in the network and network design. - Our network security team will observe the network from a defense in depth strategy to withstand any network attacks.
- The audit objective is to assist in increasing the security posture of the network.
Anzen Approach
- Read More
- First, a Data Flow Diagram (DFD) of the cloud infrastructure is reviewed.
- A Threat Model of the cloud infrastructure will be created.
- Non-Functional Security Requirements (NFSR) documents that highlight security best practices and hardening guidelines of the entire technology stack in scope will be created.
- Finally, Gap Analysis will be done.

